How to Send Messages Without Everyone Reading What You Wrote
Texting with a smartphone is how most of us talk: quick messages to friends, partners, coworkers, or family. But here’s something many people don’t realize—not all texts are private!

That message you sent last week (“Can you grab milk?”) might not seem like a big deal. But what if it had been your new address? A bank link? A private photo? Or a conversation about your health, your kid, your job?
The truth is text messages can be read by your phone company, copied while the message is traveling from phone-to-phone, and even accessed in a data breach. Here’s how that works:
- You type a message on your phone: “Running late! Be there at 7”
- Your phone sends that message to your phone company.
- The phone company forwards that message to your friend’s phone company.
- Your friend’s phone company sends that message to your friend’s phone.
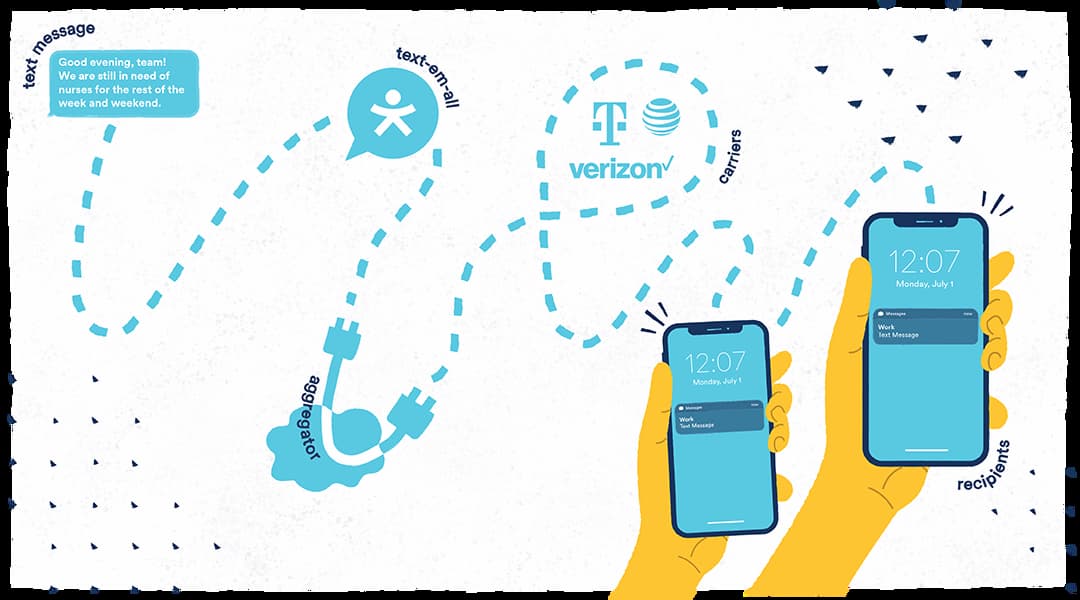
At no point in that communication chain is your text message digitally protected. Unless you’re using what is called an “encrypted” texting app, the text message is visible to:
- Your phone company
- Hackers who may tap into weak parts of that text messaging system
- Anyone who gains access to the phone company’s records
- Government agencies that request access to the phone company’s records
That’s where “encrypted messaging apps” come in! They are one of the easiest privacy upgrades you can make.
So what is Encrypted Messaging?
Encrypted texting is like putting your text message in a locked box, and only the person you’re texting has the key to that locked box. Even if a hacker, a phone company, or even a government tries to grab the box with your text message, they can’t read the text message inside because they don’t have the key to that box!
I keep hearing about end-to-end encryption?
When someone says a service provides end-to-end encryption, they mean that only you and the person you’re messaging can read the text messages because:
- The text message is locked (“encrypted”) on your phone
- The text message stays locked while it travels to the other person’s phone
- The text message is only unlocked when it arrives to the other person’s phone because only the other person has the key to unlock (“decrypt”) the message!

So, with end-to-end encryption, even if a hacker or company or government steals the text message as it travels from you to your friend, the hacker or company or government can’t read the text message because they don’t have the key to unlock the protection (“encryption”) hiding your text!
Sometimes things are only “encrypted in transit.” What does that mean? It means your message is protected while it’s being sent, but the phone or tech company sending the message can still read or store it. This is like if the post office could read the contents of every letter you sent. In comparison, for end-to-end encryption, only the sender and the receiver can see what’s inside your letter.
That’s why end-to-end encryption is one of the most powerful tools for privacy today. It helps make sure that your text message are only read by you and the person you are sending the message to.
Okay, so how do I get this encrypted messaging you’re taking about?
Let’s go over the most common encrypted messaging services:
 | What is Signal? Signal is a texting program that provides mostly secure end-to-end encryption. Signal doesn’t sell ads, and it doesn’t collect your data. It runs entirely on donations and grants. Sounds too good to be true? The catch is that both users have to have the program to enable the encryption, so you need to use Signal and you need to make your friends use Signal too. Who owns Signal? The Signal Foundation, a non-profit organization focused on privacy. |
 | What is Whatsapp? Whatsapp is heavily used outside America and was one of the first messaging services to use end-to-end encryption. However, even though your messages are encrypted, the company who owns WhatsApp (Meta, previously called Facebook) still collects metadata. What does metadata mean? Let’s say you send your friend a letter in the mail. The message is what you wrote inside the envelope. The metadata is what’s on the outside of the envelope, which includes information like: Who the message is from; Who the message is going to; The date and time the message was sent; The return address; The post office the message went through. That’s still a lot of information that Meta collects about you! Who owns WhatsApp? WhatsApp was bought by Meta, a technology company with some of the worst privacy practices on the planet. |
 | What is Telegram? Telegram is a fairly new encrypted texting service. It offers self-destruct features similar to the program Snapchat. Regular chats on Telegram are not end-to-end encrypted unless you turn on “Secret Chat.” Who owns Telegram? Telegram was started by Pavel Durov, a Russian tech entrepreneur who left Russia and moved the company abroad. Telegram is now based in Dubai, and it’s funded by private investors. |
| What is iMessage? When you send an iMessage (those blue bubble texts), Apple uses real end-to-end encryption. So, not even Apple can read what you wrote. But there’s some drawbacks: this encryption only works if both people are using Apple devices, like iPhones. Apple collects some metadata, just like Meta for WhatsApp. Also, if you back up your text messages to iCloud without turning on something called Advanced Data Protection, your messages are no longer fully private. This is because your messages will still be accessible to hackers and law enforcement if they get access to the iCloud. |
So What’s the Bottom Line When It Comes to Texting?
Use an encrypted messaging service whenever possible!
HERE is a video that discusses messaging apps.
—- Published January 2026 —-